Optimizing Azure Front Door TLS Policies: A Deep Dive into Cipher Suite Options

On April 17, 2025, Azure Front Door custom cipher suite is now generally available (GA). You can now independently define whether to enable specific TLS ciphers.
At this point in time, the TLS Policy of Azure Front Door can have 3 options:
- Default: TLS v1.2_2022
- Recommend: TLS v1.2_2023
- Balanaced: TLS custom cipher suite
Options 1: TLS v1.2_2022
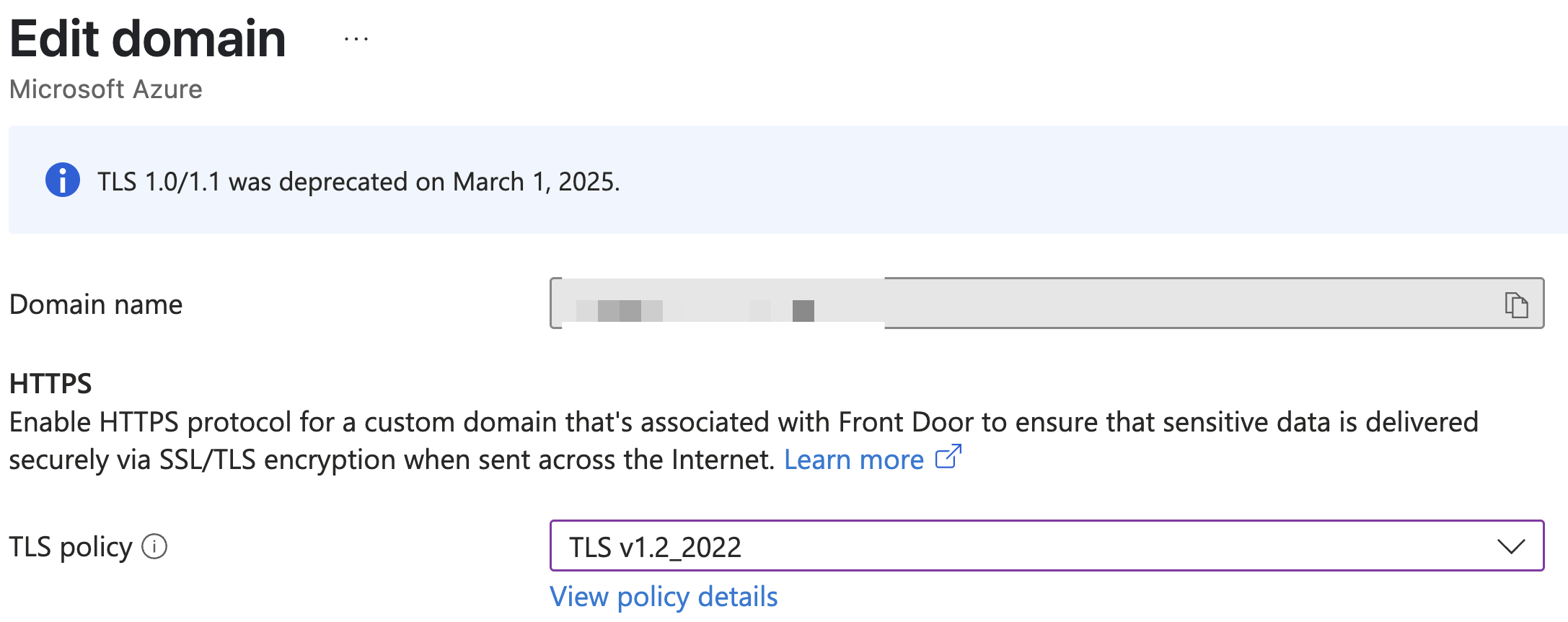
By default, you will see in the TLS Policy that you are using TLS v1.2_2022
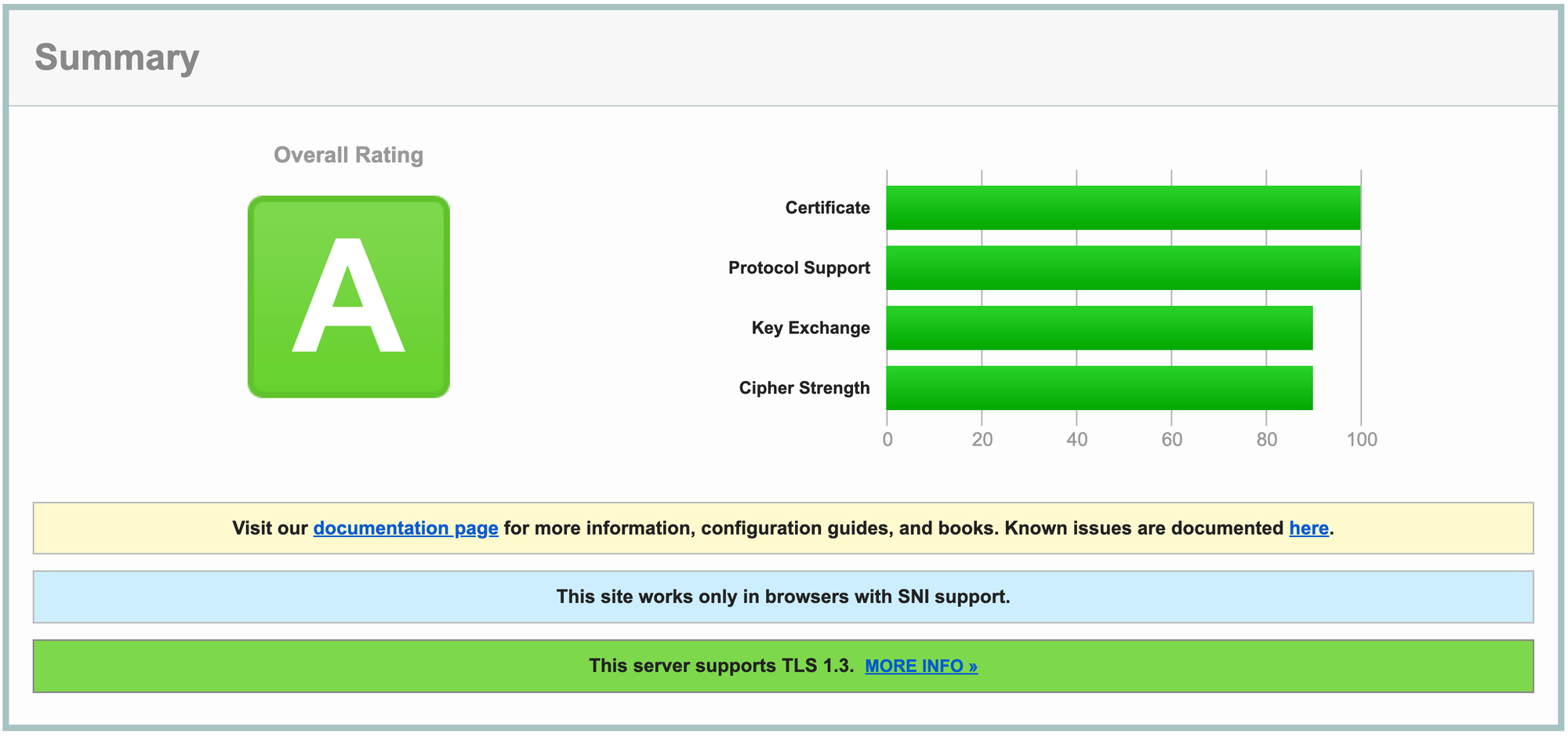
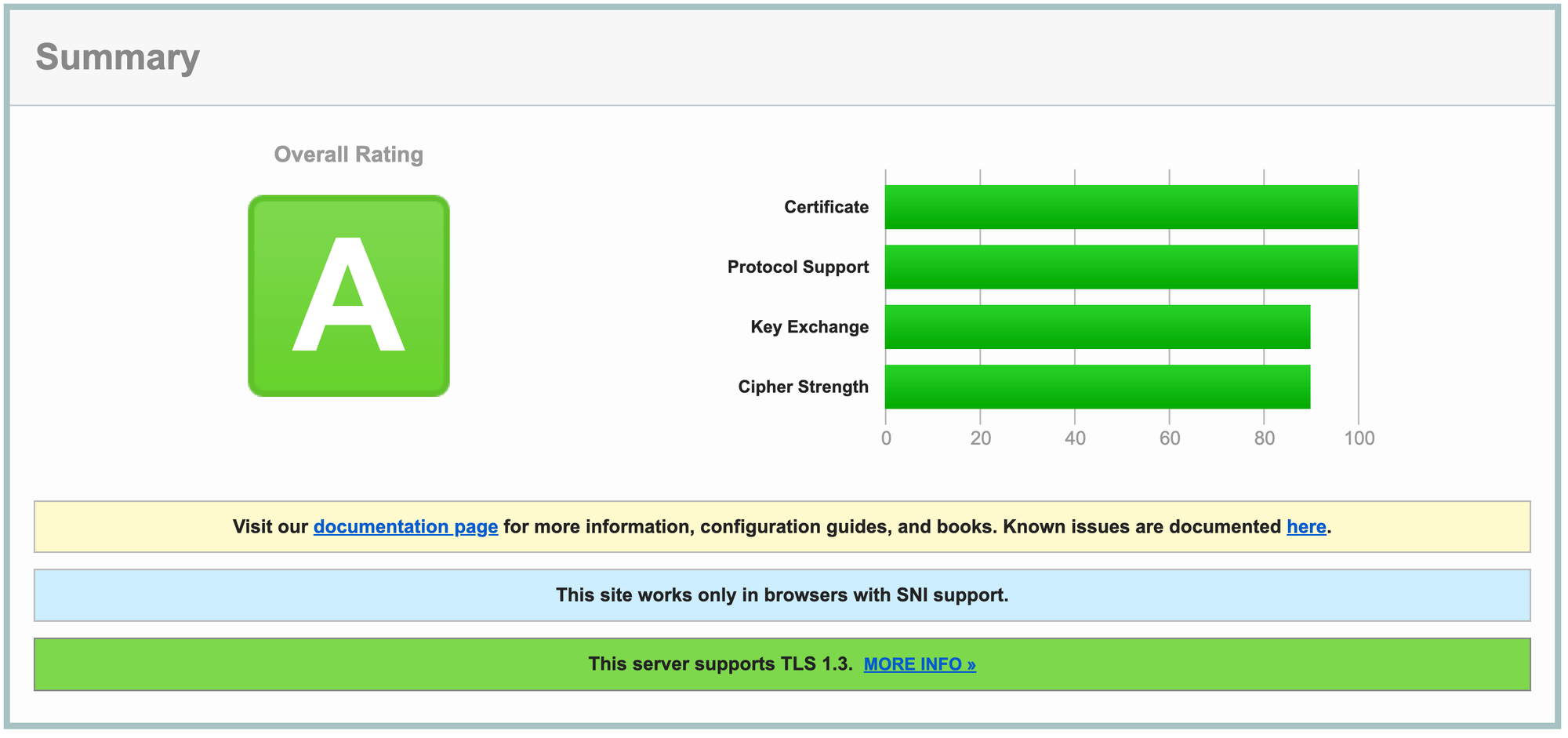
Using the online TLS testing tool provided by SSL Labs - SSL Server Test, an overall ranking of A will be obtained.
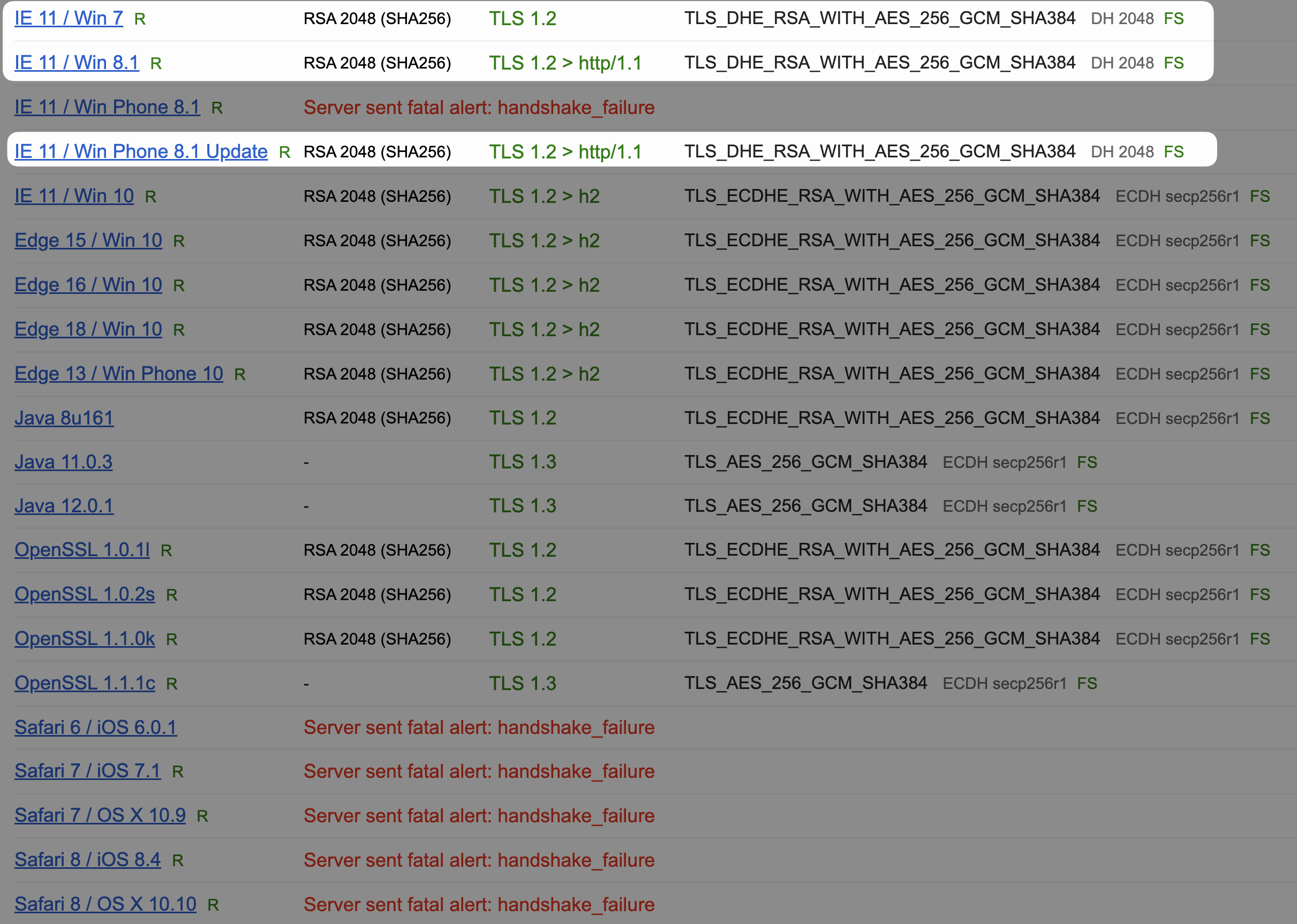
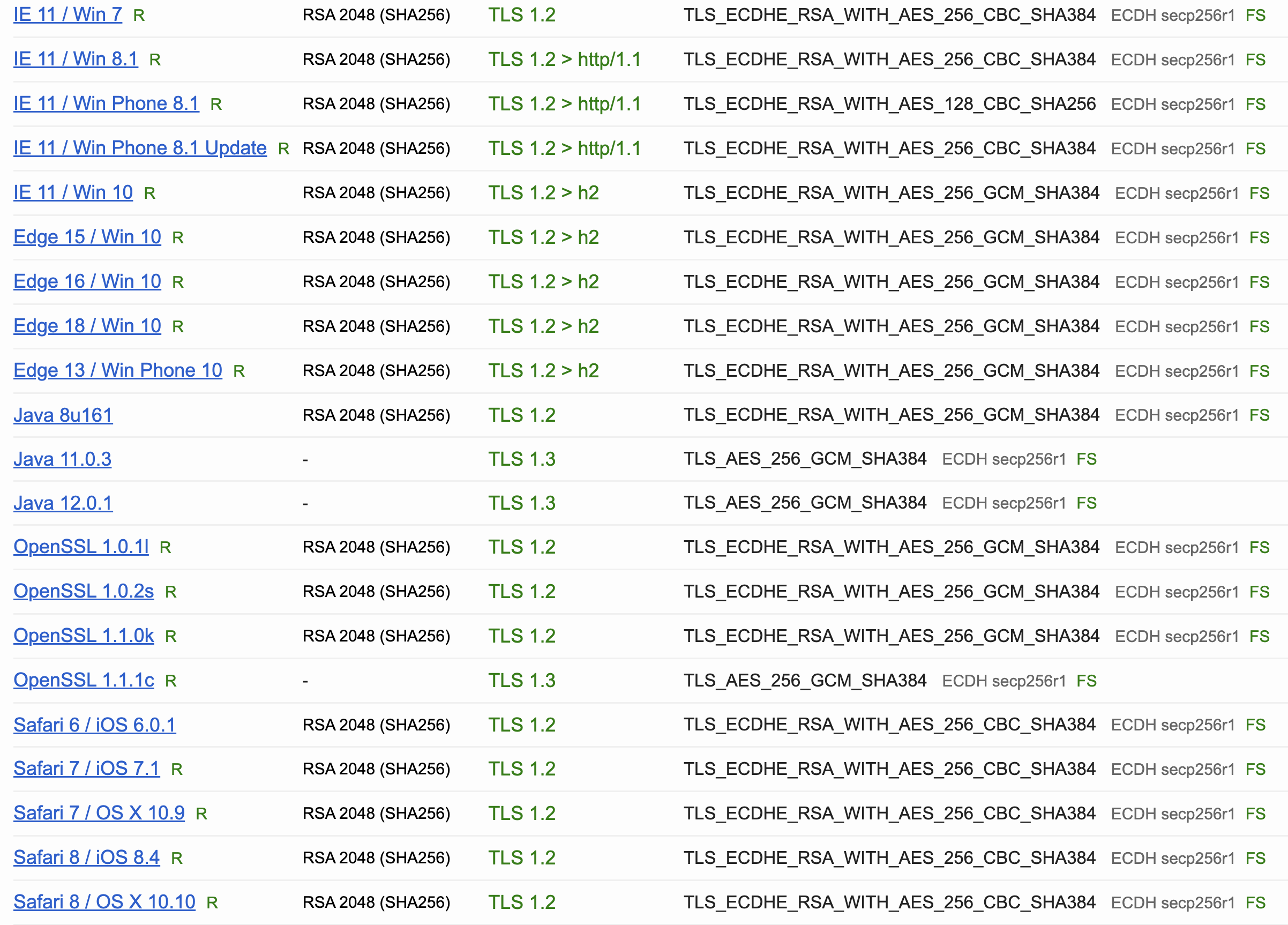
Careful examination reveals that the Cipher Suites used by Azure Front Door TLS include 2 Weak Cipher Suites
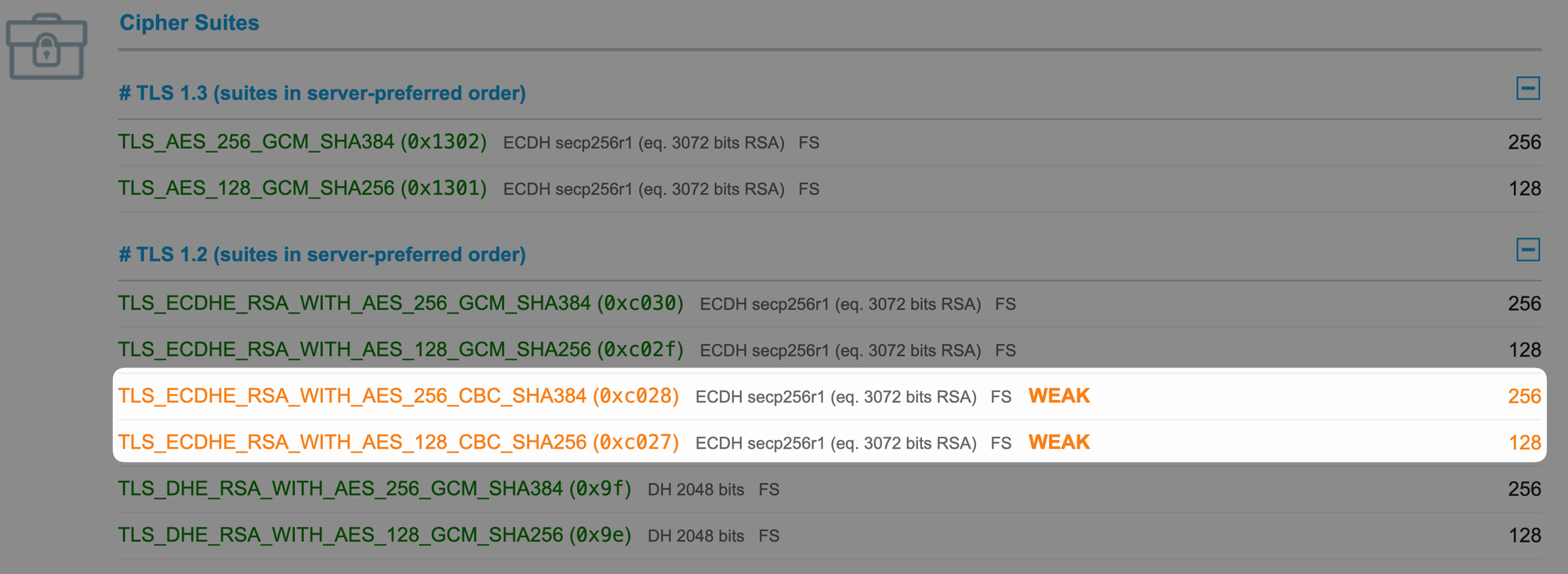
The reason is that Azure Front Door needs to support existing operating systems, such as IE /Win 7 and other earlier operating systems, which is why TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 and TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 were adopted. However, at this point in time, since very few system still use IE and Win 7, it is recommended to follow the suggestion and disable these 2 options.
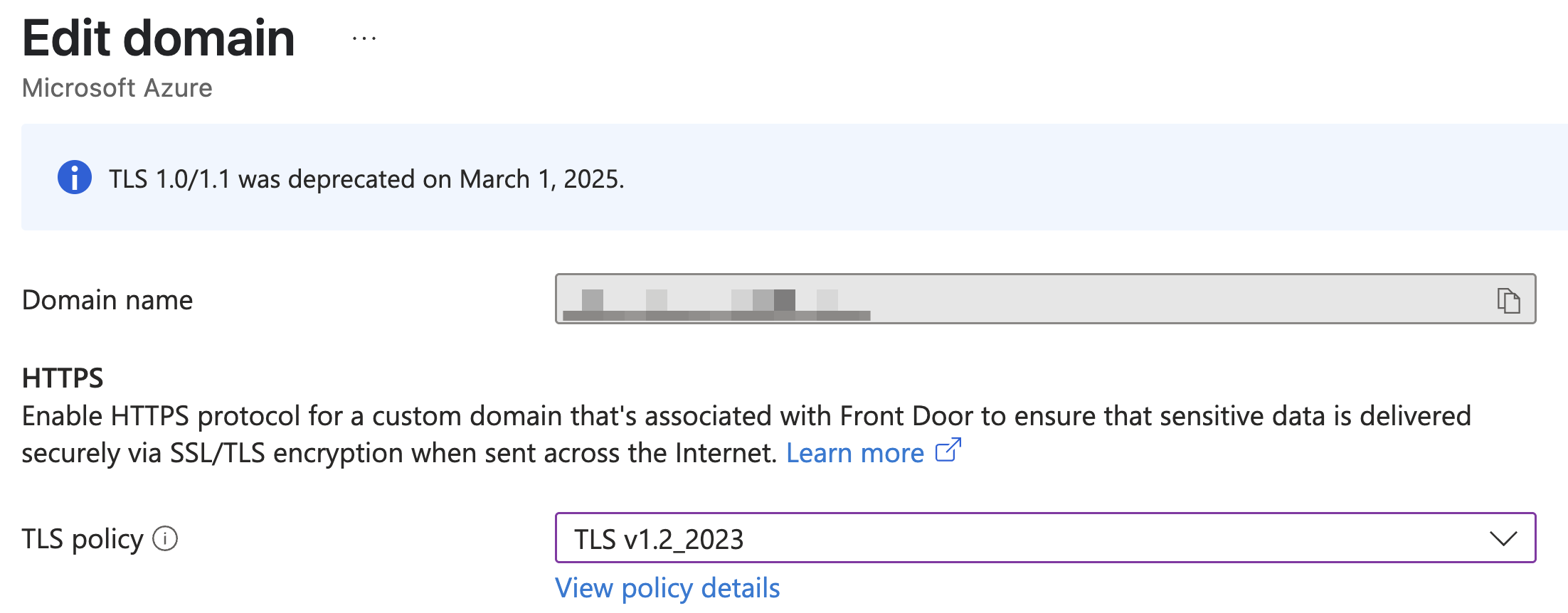
Options 2: TLS v1.2_2023
Choose TLS v1.2_2023
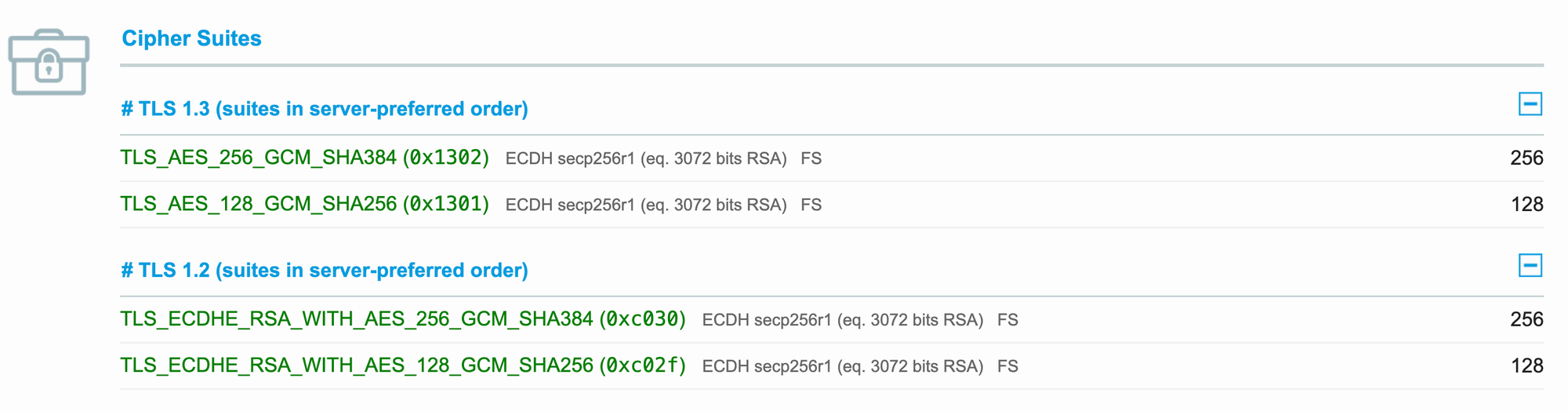
Compared to TLS v1.2_2022, TLS v1.2_2023 only allows the following 4 Cipher Suites:
- TLS_AES_256_GCM_SHA384
- TLS_AES_128_GCM_SHA256
- ECDHE-RSA-AES256-GCM-SHA384 (TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384)
- ECDHE-RSA-AES128-GCM-SHA256 (TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256)
In this situation, Cipher Suites with CBC will NOT be used, including TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 / TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256.
But the tradeoff is that the following Handshake Simulation will have issues, such as IE 11 / Win 7, where TLS handshake problems will occur.
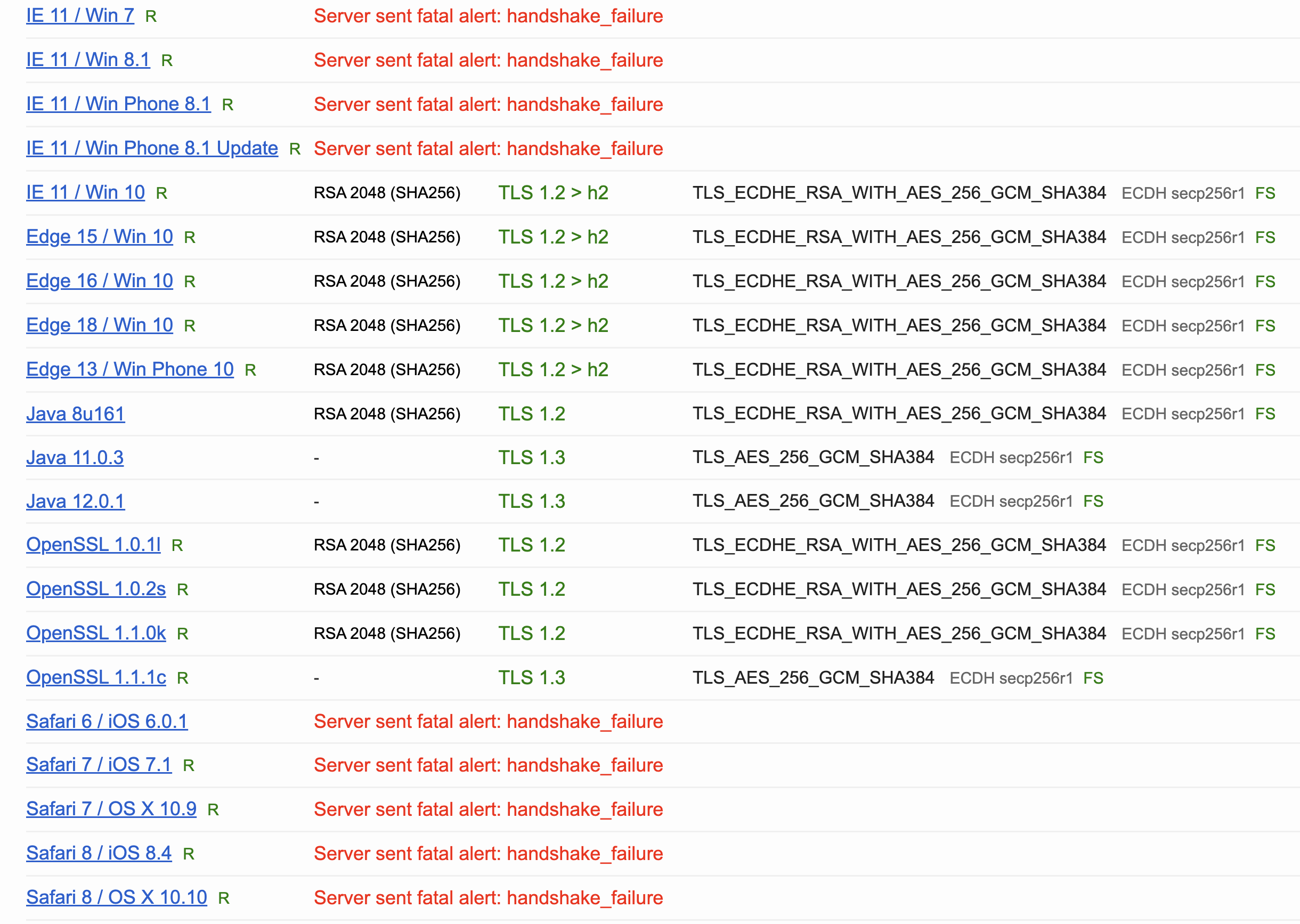
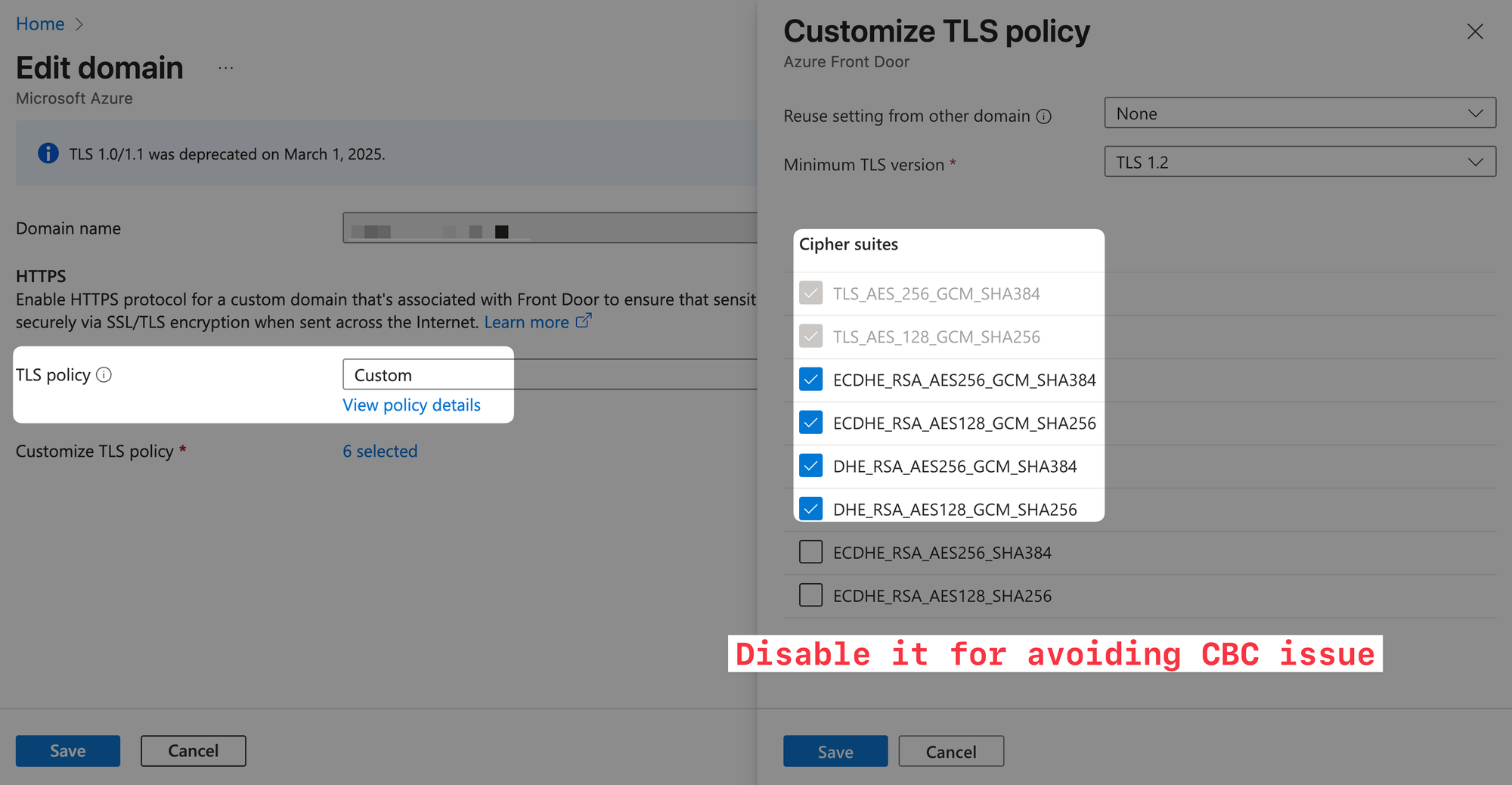
Option 3: TLS Custom Policy
To balance safety and maximize support, especially IE 11 / Win 7, you can consider using a TLS Custom Policy, selecting only the following 6 Cipher Suites:
- TLS_AES_256_GCM_SHA384
- TLS_AES_128_GCM_SHA256
- ECDHE-RSA-AES256-GCM-SHA384 (TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384)
- ECDHE-RSA-AES128-GCM-SHA256 (TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256)
- DHE-RSA-AES256-GCM-SHA384 (TLS_DHE_RSA_WITH_AES_256_GCM_SHA384)
- DHE-RSA-AES128-GCM-SHA256 (TLS_DHE_RSA_WITH_AES_128_GCM_SHA256)
The encryption methods with CBC are still not chosen, including ECDHE-RSA-AES256-SHA384 (TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384) / ECDHE-RSA-AES128-SHA256 (TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256)
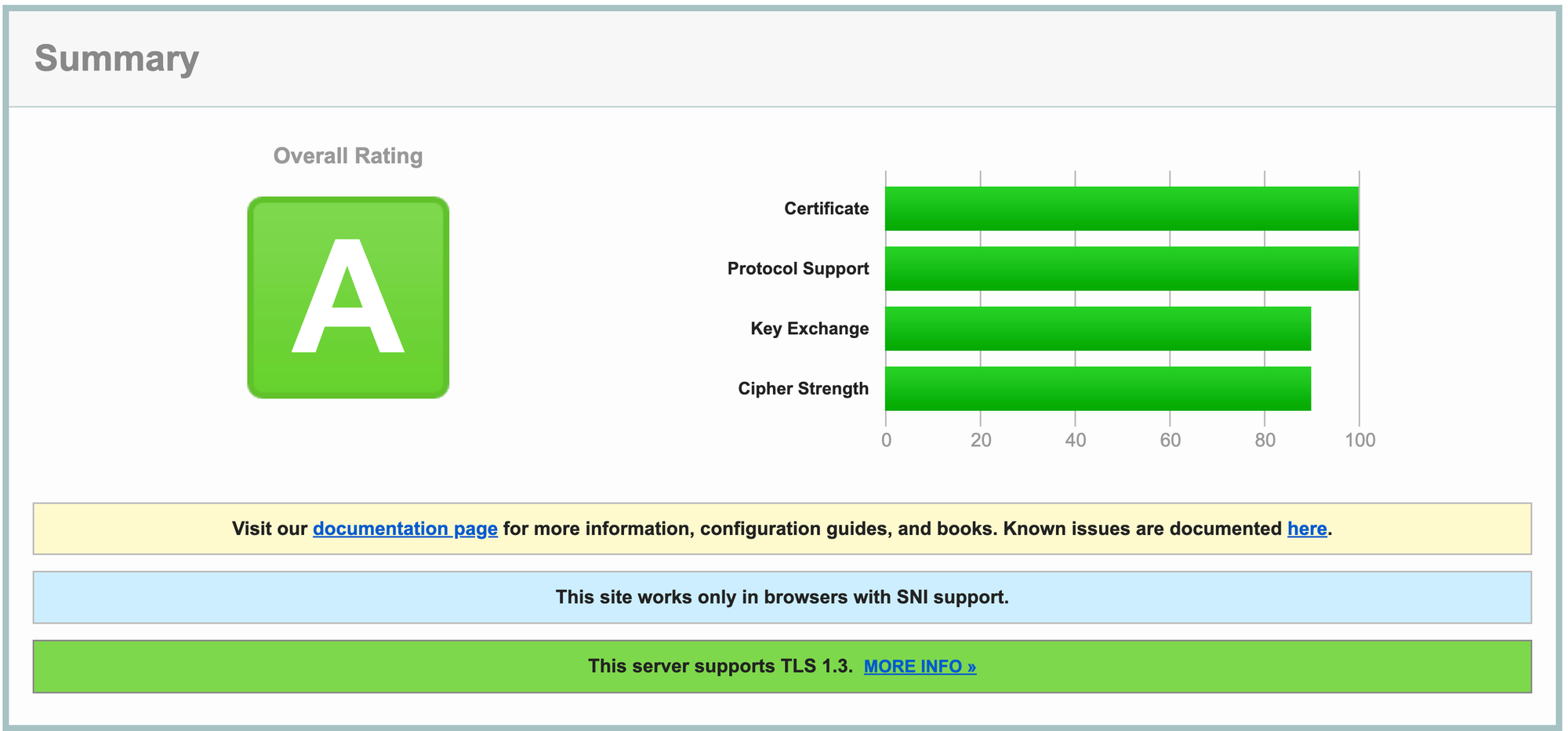
Still in A ranking
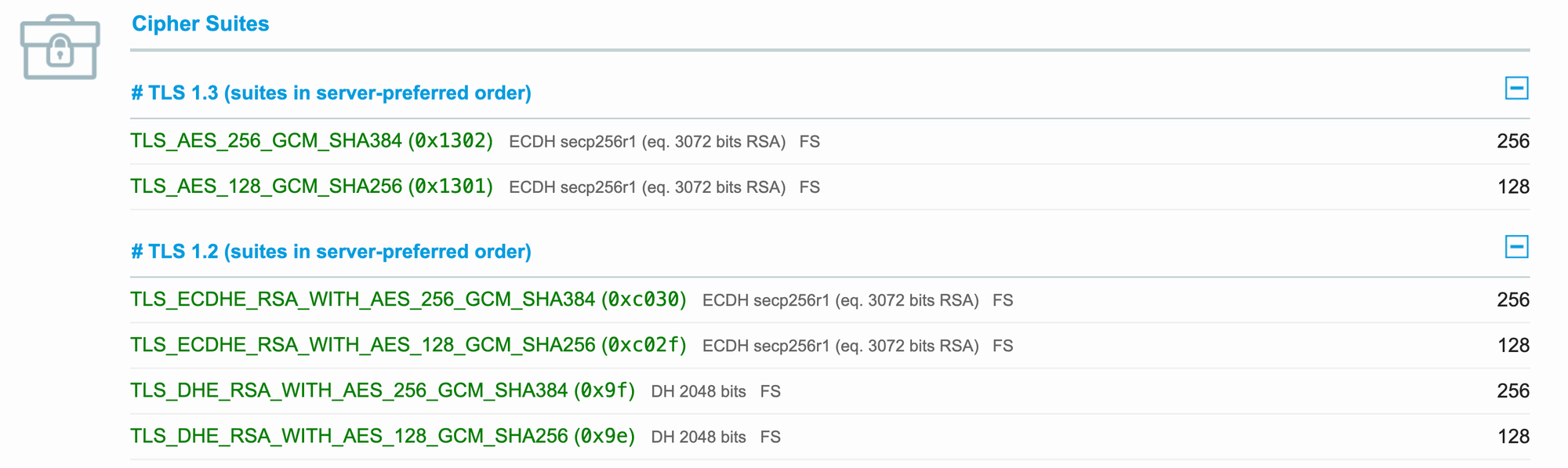
Based on this adjustment, the combination of IE 11 / Win7 can correctly establish a TLS connection through DHE-RSA-AES256-GCM-SHA384 (TLS_DHE_RSA_WITH_AES_256_GCM_SHA384) to meet the requirements