Coldpatch Container Image: Scanning Images with Trivy

Before Starting
Kubernetes Community Days Taipei 2025

Kubernetes Community Days Taipei 2025 (KCD Taipei 2025) is scheduled to take place on July 5, 2025. This is an annual event sponsored by CNCF, and we hope everyone can come and join our event together! 😸
If you want to perform a security scan on a specific container image locally and generate an assessment security report, using Aqua Security's Trivy is one of excellent choices. This project is not part of the CNCF projects, but it is highly integrated with many CNCF projects, such as Copa, Harbor and Kubernetes. Therefore, it has a place in the CNCF Landscape, categorized under Security & Compliance.

We will use the Azure AI services Diagnostic container image maintained by Microsoft for the explanation
Understand The Overall State
#!/bin/bash
docker pull mcr.microsoft.com/azure-cognitive-services/diagnostic:latest
trivy image \
--pkg-types os,library \
--table-mode summary \
mcr.microsoft.com/azure-cognitive-services/diagnostic:latest1-summary-scan-report.sh
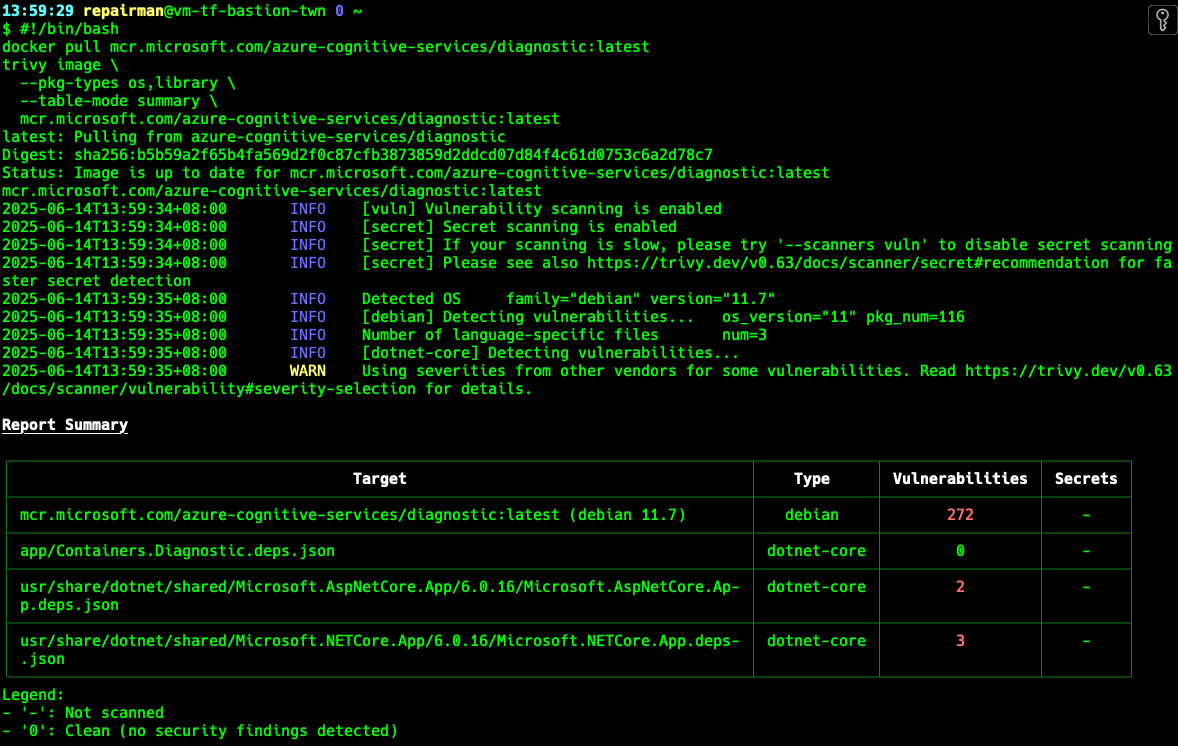
Regarding --pkg-types, the default parametes are os,libary, but somtimes when you use a container image, it is an image packaged as OS Packages + Application Packages (Language-specific).
Due to separation of responsibilities and ensuring the application can still operate after patching to the greatest extent, you may NOT want to perform repairs at the Application level. In such case, you can specify --pkg-types os to generate the report ouput.
As of 2025/06/14, Trivy supports scanning the following OS packages:
| OS | Source |
|---|---|
| Arch Linux | Vulnerable Issues |
| Alpine Linux | secdb |
| Wolfi Linux | secdb |
| Chainguard | secdb |
| MinimOS | secdb |
| Amazon Linux | Amazon Linux Security Center |
| Echo | Echo |
| Debian | Security Bug Tracker / OVAL |
| Ubuntu | Ubuntu CVE Tracker |
| RHEL | OVAL / Security Data |
| AlmaLinux | AlmaLinux Product Errata |
| Rocky Linux | Rocky Linux UpdateInfo |
| Oracle Linux | OVAL |
| CBL-Mariner | OVAL |
| Azure Linux | OVAL |
| OpenSUSE/SLES | CVRF |
| Photon OS | Photon Security Advisory |
It is known that CentOS Stream / Windows OS Container is NOT supported.
Understand Known Vulenrabilities that can be Fixed
There are a few of vulnerabilities that CANNOT be fixed even if the package are update (unpatched/unfixed). Add --ignore-unfixed, Trivy can scan container images ignoring those vulnerabilities.
#!/bin/bash
trivy image \
--pkg-types os,library \
--ignore-unfixed \
--table-mode summary \
mcr.microsoft.com/azure-cognitive-services/diagnostic:latest2-ignore-unfixed-scan-report.sh
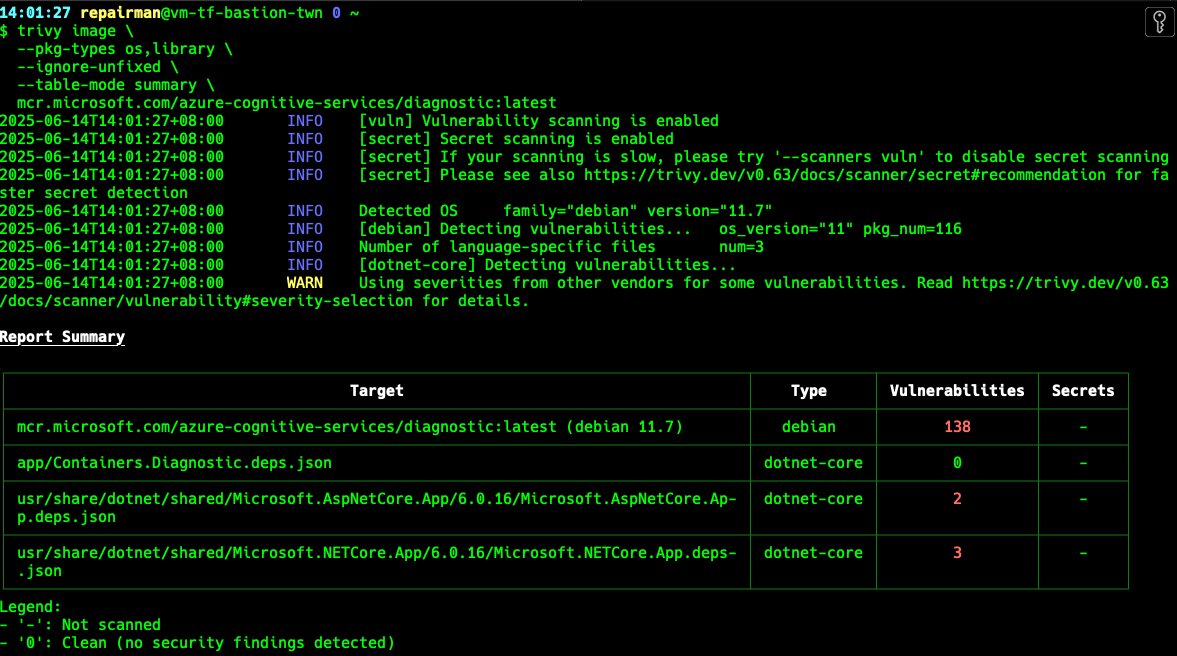
Not every vulnerability has a remediation method; Based on Trivy's documentation - Filtering, it can be understood that each vulnerability is marked with a status for better understanding.
Trivy supports the following vulnerability statuses:
| Vulnerability Statuses | Support OS | Without --ignore-unfixed | With --ignore-unfixed | Will be Detected as Vulnerability | Note |
|---|---|---|---|---|---|
| affected | All | Show in Report | Will not show | Yes | This package is affected by this vulnerability on this platform, but there is no patch released yet |
| fixed | All | Show in Report | Show in Report | Yes | This vulnerability is fixed on this platform |
| Unknown | - | Show in Report | Will not show | No | |
| not_affected | - | Show in Report | Will not show | No | This package is not affected by this vulnerability on this platform |
| under_investigation | RHEL Only | Show in Report | Will not show | No | it is currently unknown whether or not this vulnerability affects this package on this platform, and it is under investigation |
| will_not_fix | RHEL Only | Show in Report | Will not show | Yes | This package is affected by this vulnerability on this platform, but there is currently no intention to fix it (this would primarily be for flaws that are of Low or Moderate impact that pose no significant risk to customers) |
| fix_deferred | RHEL / Debian | Show in Report | Will not show | Yes | This package is affected by this vulnerability on this platform, and may be fixed in the future |
| end_of_life | RHEL / Debian | Show in Report | Will not show | Yes | This package has been identified to contain the impacted component, but analysis to determine whether it is affected or not by this vulnerability was not performed |
From the table above, you only need to focus on 2 Vulnerability Status: affected and fixed
Create report for Copa
Since the subsequent post will introduce the container patch tool - Copa, which requires the report generated by Trivy scanning, we need to specifically export it in JSON format.
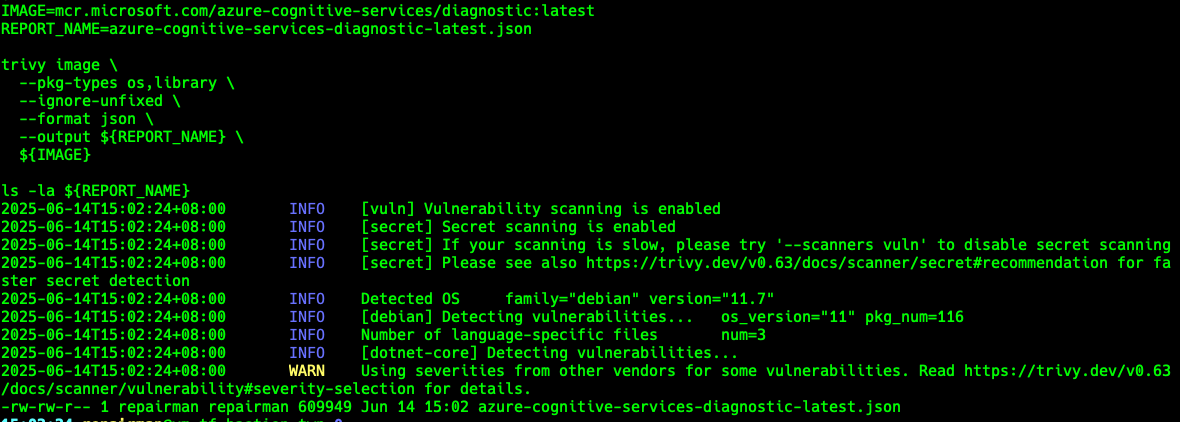
#!/bin/bash
IMAGE=mcr.microsoft.com/azure-cognitive-services/diagnostic:latest
REPORT_NAME=azure-cognitive-services-diagnostic-latest.json
trivy image \
--pkg-types os,library \
--ignore-unfixed \
--format json \
--output ${REPORT_NAME} \
${IMAGE}
ls -la ${REPORT_NAME}3-generate-report-as-json.sh
TL;DR
#!/bin/bash
IMAGE=mcr.microsoft.com/azure-cognitive-services/diagnostic:latest
REPORT_NAME=azure-cognitive-services-diagnostic-latest.json
# Download the specified container image
docker pull ${IMAGE}
# Generate a report for the specified container image
trivy image \
--pkg-types os,library \
--format json \
--quiet \
--output ${REPORT_NAME} \
${IMAGE}
# Show result
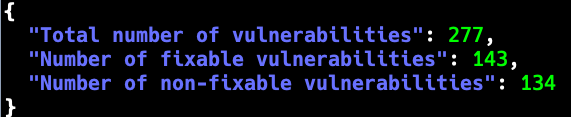
jq '
[ ..
| .Vulnerabilities?
| .[]?
] as $all |
{
"Total number of vulnerabilities": ($all | length),
"Number of fixable vulnerabilities": ($all | map(select(.FixedVersion != null and .FixedVersion != "")) | length),
"Number of non-fixable vulnerabilities":($all | map(select(.FixedVersion == null or .FixedVersion == "")) | length)
}
' ${REPORT_NAME}understand-your-container-image.sh
Appendix: Install Trivy
#!/bin/bash
sudo apt-get install wget gnupg
wget -qO - https://aquasecurity.github.io/trivy-repo/deb/public.key | gpg --dearmor | sudo tee /usr/share/keyrings/trivy.gpg > /dev/null
echo "deb [signed-by=/usr/share/keyrings/trivy.gpg] https://aquasecurity.github.io/trivy-repo/deb generic main" | sudo tee -a /etc/apt/sources.list.d/trivy.list
sudo apt-get update
sudo apt-get install trivyinstall-trivy.sh



