Analyzing TLS encrypted traffic through SSLKEYLOGFILE

Based on TLS - Wireshark Wiki, Wireshark supports TLS decryption, and the 3 methods are as follows:
- Key log file using (pre)-master secrets
- Decrpyion using an RSA private key
- Decrption using Pre-shared-key (PSK)
However, the most common method should be Method 1: Key log file using (pre)-master secrets, as it is available in Firefox, Edge, Chrome, curl and OpenSSL. The key log file is a text file generated by application when the SSLKEYLOGFILE evnironment variable is set.
If you wan to use method 2, you need to have an RSA private key first, but in most cases, you won't have it unless you are the administrator responsible for manageing TLS certificates.
(Pre)-master secrets
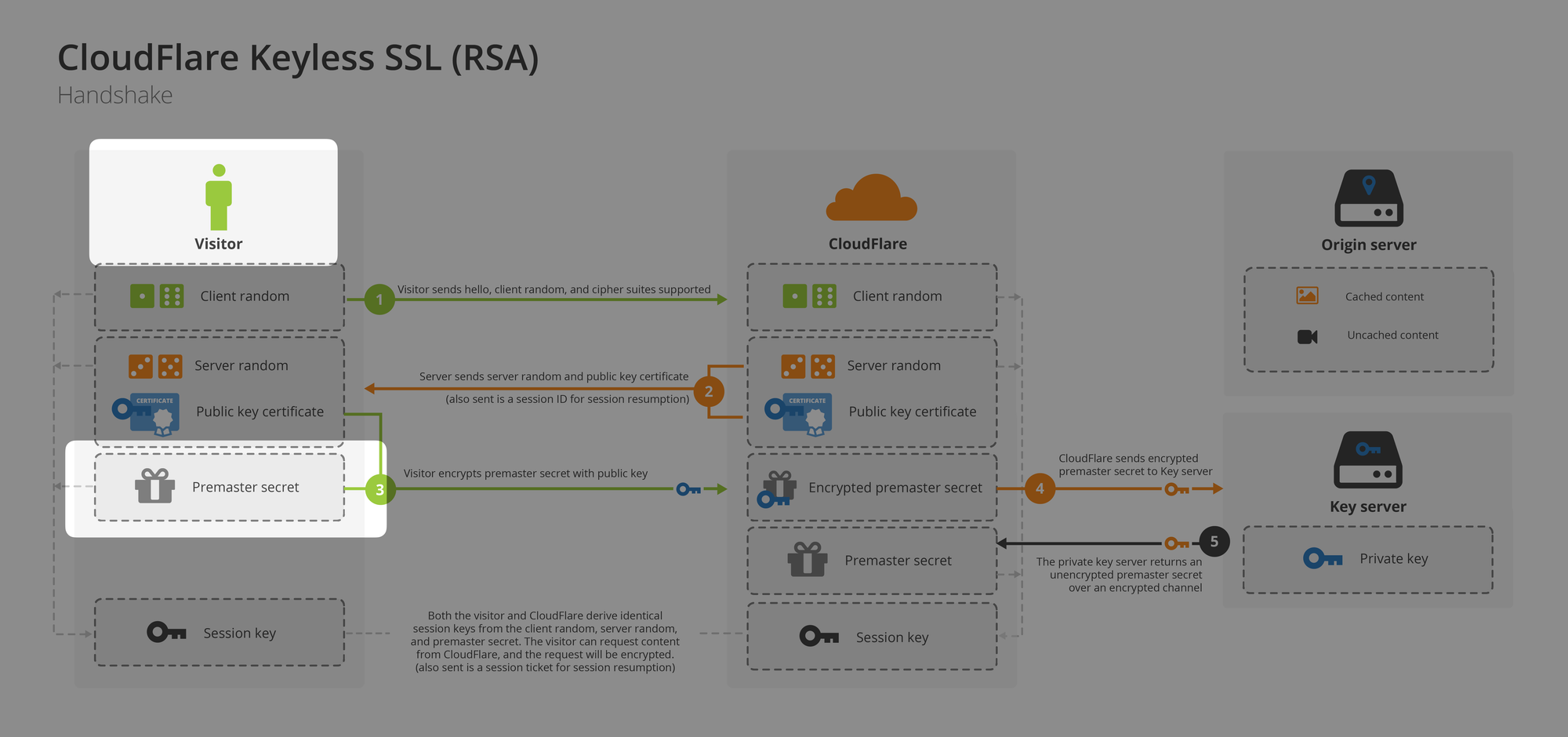
In network analysis and troubleshooting, if the (pre)-master secrets can be obtained, Wireshark can calculate the master secrets and session keys, thereby decrypting the captured TLS packet contents. This is very useful for debugging HTTPS communications or analyzing the encrypted traffic of malware.
Below, I will explain a few solutions for setting (pre)-master secrets
Solution 1: Use -keylogfile feature in OpenSSL s_client
This approach is applicable when you only have a CLI environment and no desktop environment, directly using openssl s_client for operaiotns
#!/bin/bash
openssl s_client -connect blog.blackair.io:443 -keylogfile ./sslkeys.log
# or
# openssl s_client -connect examaple.com:443 -keylogfile ./sslkeys.logYou can see the `CONNECTED(00000006)` , and you can manually input an HTTP/1.1 request
GET / HTTP/1.1
Host: blog.blackair.ioHTTP Command
Press Enter twice to see the server's respone, then use Ctrl+C to terminate the TLS connection. At this point, sslkeys.log will contain the (Pre)-Master-Secret
Of course, you can also use tcpdump to record the TLS handshake process
#!/bin/bash
sudo tcpdump -i any host blog.blackair.io and tcp port 443 -w tls_blog.pcaptcpdump
Solution 2:
Strongly recommend referring to the official Wireshark documentation
Step-by-step instructions to decrypt TLS traffic from Microsoft Edge in Wireshark on MacOS:
- Close the browser completely (check your task manager just to be sure).
#!/bin/bash
pkill Microsoft\ Edge
pkill
- Set environment variable
SSLKEYLOGFILEto the absolute path of a writable file - Start the Microsoft Edge browser
- Verify that the location from step 2 is created
#!/bin/bash
export SSLKEYLOGFILE=$HOME/Desktop/keylogfile.txt
echo $SSLKEYLOGFILE
open -a open -a Microsoft\ EdgeFor MacOS + Edge
- In Wireshark, go to Wireshark -> Preferences -> Protocols -> TLS, and change the (Pre)-Master-Secret log filename preference to the path from step 2.
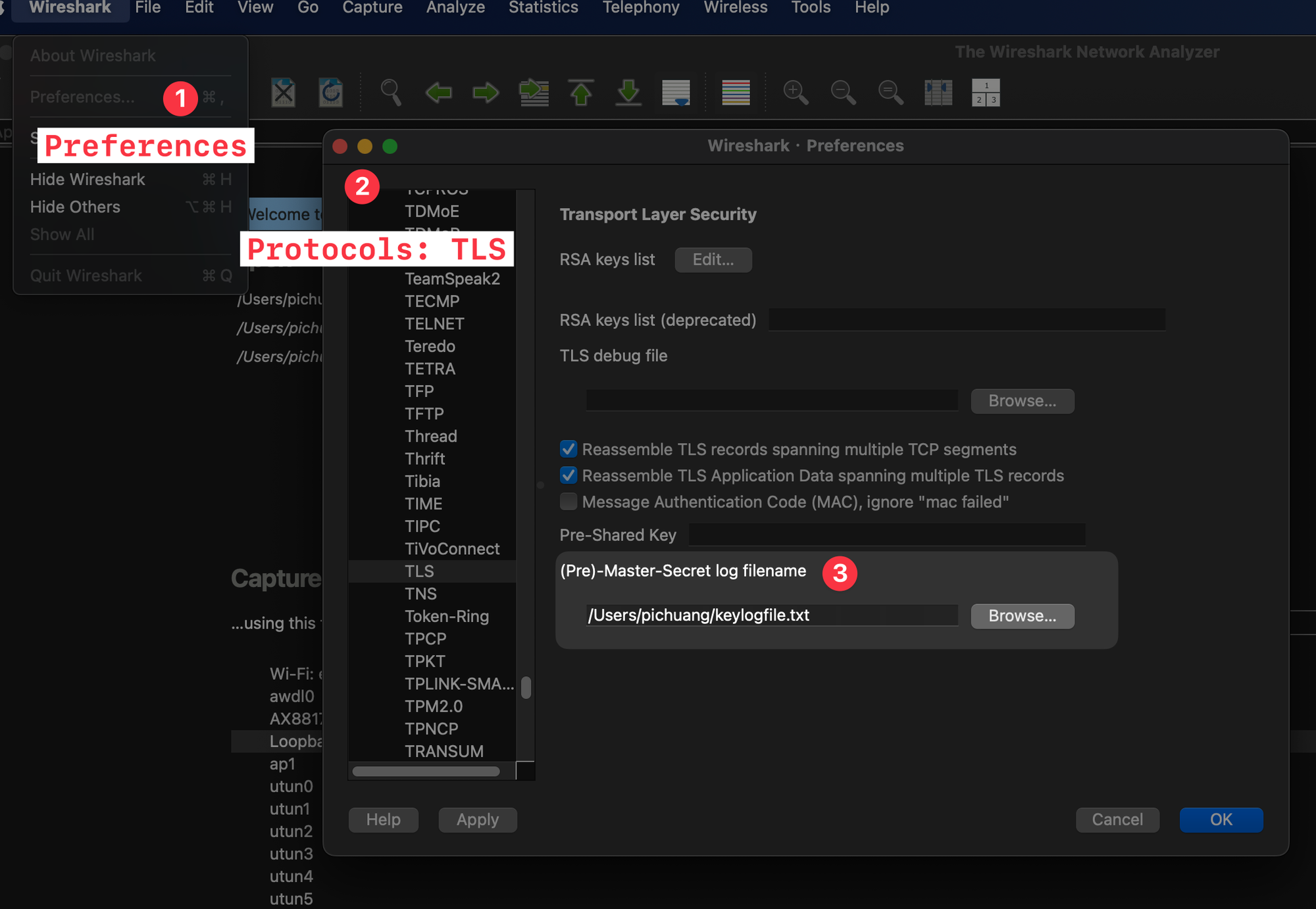
- Start the Wireshark capture
- Open https://blog.blackair.io or others TLS website
- Observe TLS Handshake
tls.handshake.type == 1 || tls.handshake.type == 2This display filters out all TLS Hello stage handshake packets, making it easier to quickly locate the initial negotiation packets
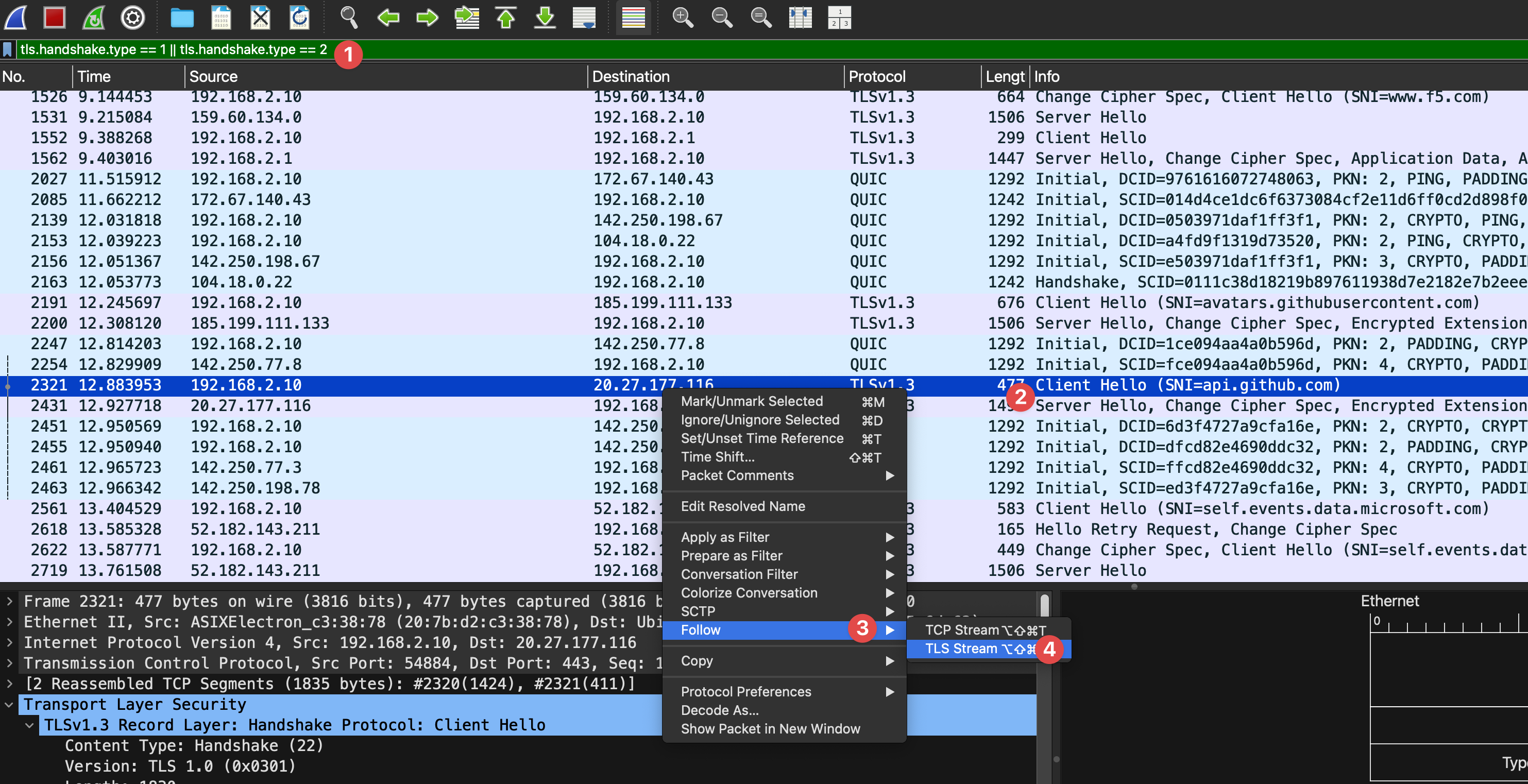
- Query specific TLS SNI
tls.handshake.extensions_server_name == "blog.blackair.io"Since my service is placed behind a CDN, the IP will change, but the corresponding packets can be found by querying the SNI.
Bonus: Only capture the bidirectional traffic between the two
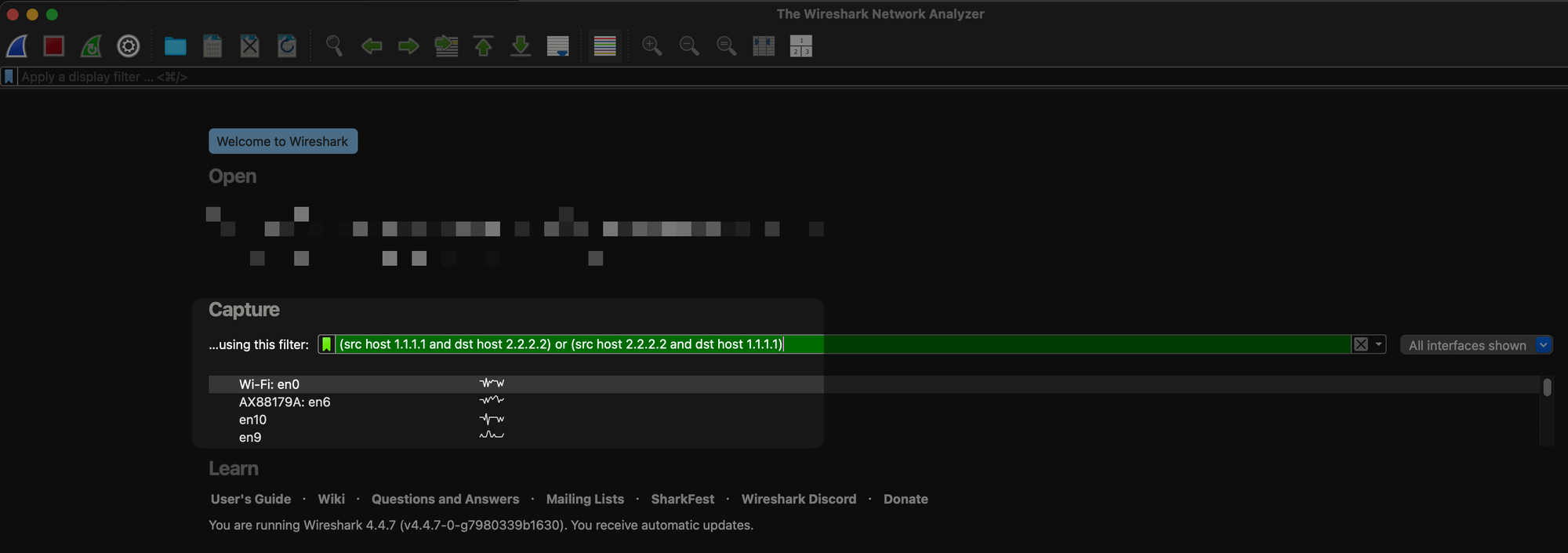
(src host 1.1.1.1 and dst host 2.2.2.2) or (src host 2.2.2.2 and dst host 1.1.1.1)Phil's Memo
Recently, Wireshark Foundation officially launched the Wireshark Certified Analyst WCA-101, which is highly distinctive.
